What is HAProxy? HAProxy fundamentals.
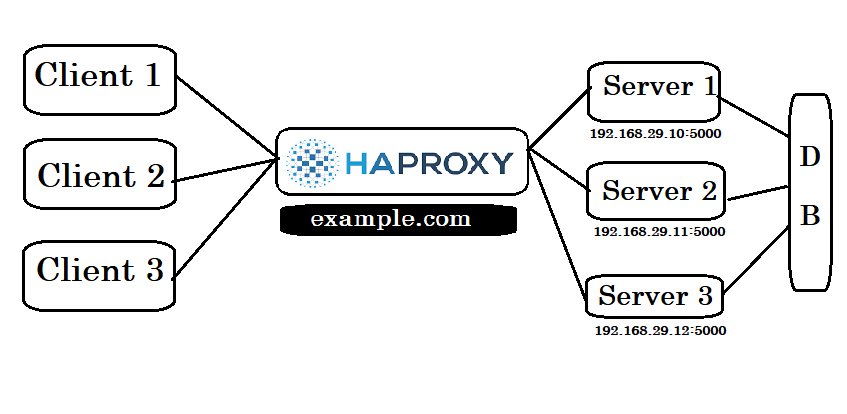
HAProxy (High Availability Proxy) is a free, open-source software written in C. It is renowned for providing high availability, load balancing, and proxying at both Layer 4 (transport layer) and Layer 7 (application layer) of the OSI model. HAProxy is highly efficient in terms of processor and memory usage and is widely used for its speed and reliability.
So we can say that HAProxy is open source tool we use for proxying and load balancing. It provides both layer 4 and layer 7 proxying.
Key Features of HAProxy
- High Availability: Ensures that services remain available even if some of the servers fail.
- Load Balancing: Distributes incoming traffic across multiple servers to optimize resource usage, improve response times, and ensure no single server is overloaded.
- Proxying: Acts as an intermediary for requests from clients seeking resources from servers, improving security and performance.
- Layer 4 and Layer 7 Load Balancing: Supports TCP and HTTP load balancing, providing flexibility in handling different types of traffic.
- Scalability: Can handle a large number of connections simultaneously, making it suitable for high-traffic websites.
Load Balancing Explained
Load balancing is the process of distributing tasks across multiple computing resources to optimize their usage, improve response times, and avoid overloading any single resource. Effective load balancing ensures that no server is overwhelmed while others remain idle.
Architecture Without Load Balancing
In a typical application architecture without load balancing, a single server handles all incoming requests. This setup can lead to several issues:
- Single Point of Failure: If the server fails, the entire application becomes unavailable.
- Scalability Issues: As traffic increases, the server may become overloaded, leading to performance degradation or failure.
- Inefficient Resource Utilization: Without load balancing, some resources may remain underutilized while others are overburdened.
Benefits of Using HAProxy
- Increased Availability: By distributing traffic across multiple servers, HAProxy ensures that services remain available even if some servers fail.
- Improved Performance: Load balancing helps optimize resource usage, reducing latency and improving response times.
- Enhanced Scalability: HAProxy can easily scale to handle increased traffic by adding more servers to the pool.
- Security: Acting as a proxy, HAProxy can help protect backend servers from direct exposure to the internet.
Example: HAProxy in Action
Imagine a web application receiving high traffic. Without load balancing, a single server would struggle to handle the load, potentially leading to downtime and lost business opportunities. By implementing HAProxy, traffic can be distributed across multiple servers, ensuring that no single server is overwhelmed, improving both performance and reliability.
Here are some technical fundamental terms related to HAProxy explained in simple words:
- Reverse Proxy
A reverse proxy is like a middleman that sits between the users and the servers. When users make a request (like visiting a website), the reverse proxy receives it and then forwards it to one of the servers. The server's response goes back through the proxy to the users. This helps in managing traffic and hiding the details of the servers. (like suppose server running on IP:5000 we can hide details such as port and etc. by assigning a domain to it and using proxying) - Load Balancer
A load balancer distributes incoming requests across multiple servers. Imagine a queue with many counters; a load balancer makes sure each counter has a similar number of people to serve. This way, no single counter (or server) gets overwhelmed. - Layer 4 (Transport Layer) Load Balancing
Layer 4 load balancing deals with the data transfer part of network communication. It's like directing cars at a traffic light, regardless of who is inside. It looks at information like IP addresses and port numbers to decide where to send the data. - Layer 7 (Application Layer) Load Balancing
Layer 7 load balancing looks deeper into the data being sent, like reading a letter to see who it's for and what it's about before delivering it. It can make decisions based on content, like URLs or cookies, to route requests more intelligently. - Health Checks
Health checks are tests run by the load balancer to see if the servers are working correctly. It's like a doctor checking a patient's vital signs. If a server isn't healthy, it stops sending traffic to that server until it's fixed. - Failover
Failover is a process where if one server goes down, the load balancer automatically redirects traffic to another server. It's like having a substitute teacher step in when the regular teacher is sick, so the class can continue without interruption. - SSL Termination
SSL termination is when the load balancer handles the encryption and decryption of data instead of the servers. It's like having a secure mailbox where letters are opened and read safely before being handed over to the recipient. - Backend Servers
Backend servers are the actual servers that store and process data. They are the ones doing the heavy lifting behind the scenes, like kitchen staff in a restaurant who prepare the food. - Frontend
The frontend is what the users interact with, like the waiter in a restaurant taking orders. In HAProxy, the frontend receives the requests from users and passes them to the appropriate backend servers. - Sticky Sessions
Sticky sessions (or session persistence) ensure that a user's requests are always sent to the same server. It's like always having the same waiter every time you visit a restaurant, so they remember your preferences. - Configuration File
The configuration file is where all the settings and rules for HAProxy are defined. It's like a recipe book that tells HAProxy how to handle different types of traffic, which servers to use, and what actions to take under various conditions. - ACL (Access Control List)
ACLs are rules that define which traffic is allowed or denied. It's like a guest list at a party, determining who can enter and who can't based on specific criteria. - Rate Limiting
Rate limiting controls the number of requests a user can make in a given period. It's like a speed limit sign that prevents cars from going too fast to ensure safety and smooth traffic flow.
Now let's study few more key terms for HAProxy
TLS Termination vs. TLS Passthrough
1. TLS Termination:
- Explanation: TLS (Transport Layer Security) termination is when the load balancer (like HAProxy) handles the encryption and decryption of traffic. This means the data is decrypted at the load balancer before being forwarded to the backend servers.
- Analogy: It's like opening a sealed letter at the post office, reading its contents, and then sending the message in a simpler form to the recipient.
- Benefits: Reduces the workload on backend servers since they don’t need to handle encryption/decryption, and allows for inspection and routing of traffic based on content.
2. TLS Passthrough:
- Explanation: In TLS passthrough, the load balancer passes encrypted traffic directly to the backend servers without decrypting it. The backend servers handle the encryption and decryption.
- Analogy: It's like passing a sealed letter through multiple checkpoints without opening it until it reaches the final recipient.
- Benefits: Maintains end-to-end encryption, ensuring data privacy and security, but prevents the load balancer from inspecting the traffic content.
HAProxy Modes
1. TCP Mode (Layer 4):
- Explanation: HAProxy operates at the transport layer, dealing with raw data packets. It doesn't look into the contents of the traffic.
- Analogy: It's like a traffic cop directing cars based on their license plates and types but not looking inside the cars.
- Use Cases: Suitable for applications like SSH, database connections, and any other non-HTTP services.
2. HTTP Mode (Layer 7):
- Explanation: HAProxy operates at the application layer, inspecting the contents of the traffic (like headers and data) before making routing decisions.
- Analogy: It's like a customs officer checking the contents of packages to decide where they should go.
- Use Cases: Ideal for web applications where decisions need to be made based on URL, headers, or cookies.
3. TCP Health Checks:
- Explanation: HAProxy performs health checks at the transport layer by establishing a TCP connection to the server.
- Analogy: It's like checking if a phone line is open without having a conversation.
- Benefits: Ensures that the server is reachable and capable of accepting connections.
4. HTTP Health Checks:
- Explanation: HAProxy performs health checks at the application layer by sending HTTP requests to the server and checking the responses.
- Analogy: It's like making a phone call and asking a specific question to see if the person on the other end can respond correctly.
- Benefits: More thorough than TCP health checks, as it can verify that the server is not only reachable but also functioning correctly at the application level.
Conclusion
HAProxy is a powerful and efficient tool for managing high availability, load balancing, and proxying for web applications. Its ability to handle both Layer 4 and Layer 7 traffic makes it versatile and essential for high-traffic websites and services. By using HAProxy, businesses can ensure their applications remain available, performant, and scalable.
